Social engineering operation from Iran poses a threat to researchers, journalists, and academics.
As part of a new social engineering operation to look for sensitive information, hackers with ties to the Iranian government have been going after experts in Middle Eastern politics, nuclear security, and genomic research.
Cyber operations tracked as APT42, Charming Kitten, and Phosphorus largely coincide with those attributed to the threat actor TA453, according to Proofpoint, an enterprise security firm.
According to Proofpoint’s analysis, a typical TA453 campaign involves the threat actor posing as a person working in collaboration with the target, such as a journalist or policy related figure. Scholars, politicians, diplomats, journalists, and advocates for human rights have all been TA453’s previous victims. It is common for TA453 activity to begin with seemingly harmless discussions before leading to URLs that harvest credentials.
How does it work?
Initially, the Iranian Islamic Revolutionary Guard Corps (IRGC) sends out phishing emails in the guise of actual employees at Western foreign policy research groups with the ultimate goal of gaining intelligence on the West (IRGC).
“Sock Puppets” have been used to impersonate researchers at the Pew Research Center, the Foreign Policy Research Institute (FRPI), the Chatham House in the United Kingdom, and Nature, a scientific publication.
Proofpoint calls this type of phishing attempt “Multi-Persona Impersonation (MPI),” in which the threat actor uses not just one but many actor-controlled personas in a single email discussion to increase the likelihood of success.
A Microsoft Office document, supposedly alluding to a conflict between Russia and the United States, is downloaded once the victim replies to the original email, which contains a dangerous OneDrive link.
Who has been targeted by this campaign?
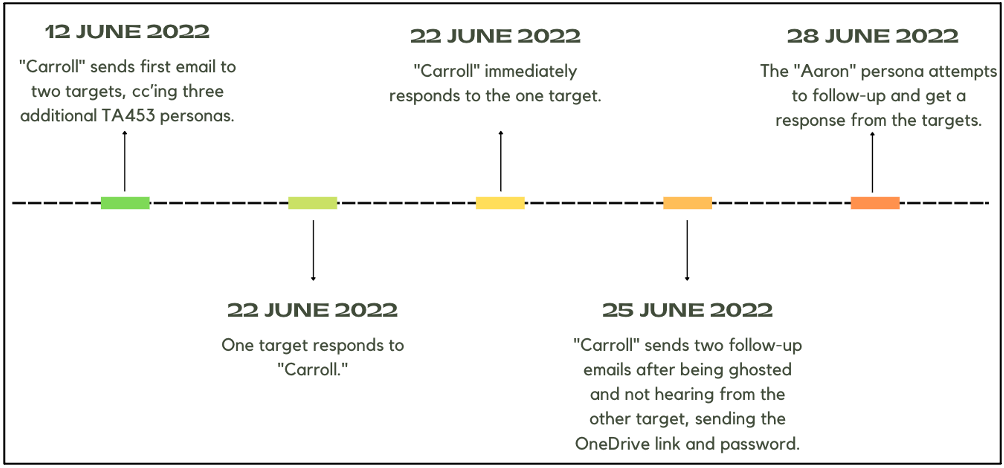
The TA453 alias “Carroll Doherty” contacted a prominent academic working on nuclear weapons control in June 2022 to discuss the possibility of a conflict between the United States and Russia. Since the persona didn’t stop at two targets at the same university, this campaign may be seen as a development of TA453’s MPI approach. In addition to the original recipients, “Carroll” copied “Daniel Krcmaric,” “Aaron Stein,” and “Sharan Grewal” on the email.
There was an initial reply from one of the targets to the outreach email, but then “Carroll” disappeared. After waiting about a week for a reply from the intended recipient, “Carroll” was prompt to send along a OneDrive link to the aforementioned article. The link led to a.docx file with the headline “The potential US-Russia war”, which injects a “Korg” file into the users device.
After downloading Korg using a remote template injection, three macros may collect usernames, a list of current processes, and the victims’ public IP addresses.
The actor posing the threat has previously engaged in similar impersonation efforts. SpoofedScholars, a phishing campaign exposed by Proofpoint in July 2021, pretended to be affiliated with the University of London’s School of Oriental and African Studies and targeted people interested in Middle East politics in the United States and the United Kingdom (SOAS).
These new campaigns directed at academics, researchers, and journalists signify an increase in malicious activity by hackers to source information and data.
Proofpoint has advised high-level targets to be critical of emails they receive and to verify the credentials of the “researchers” or journalists reaching out.
“Researchers involved in international security, particularly those specializing in Middle Eastern studies or nuclear security, should maintain a heightened sense of awareness when receiving unsolicited emails.For example, experts that are approached by journalists should check the journalist’s or their publication’s website to see if the email address belongs to them.”
Proofpoint, 13th September 2022